I obtained my Ph.D. in 2024 and my B.Eng. in 2019 from the College of Electrical Engineering at Zhejiang University, and I currently work as a security researcher.
My doctoral research is under the guidance of Prof. Wenyuan Xu and Prof. Yanjiao Chen at ZJU. Recently, I successfully defended my Ph.D. thesis. My research interests revolve around AI (for) security and privacy, with a particular focus on the security and safety of (multimodal) large language models (LLMs) recently. I have contributed to several publications in leading security conferences such as IEEE S&P, USENIX Security, ACM CCS, and NDSS. I am open to academic collaborations and welcome discussions regarding potential research partnerships.
The template for this page is credited to AcadHomepage.
🔥 News
- 2024.08.31: 🎉🎉 Accepted paper for presentation at the NDSS Symposium 2025!
- 2024.08.24: 🎉🎉 Accepted paper for presentation at the ACM Conference on Computer and Communications Security 2024!
- 2024.05.31: 🎉🎉 Successfully defended my Ph.D. thesis!
- 2024.05.24: 🎉🎉 One paper is accepted by ACM CCS 2024!
- 2024.05.20: 🎉🎉 Attended the 45th IEEE Symposium on Security and Privacy in San Francisco, CA, from May 20th to 23rd.
- 2024.04.04: 🎉🎉 One paper is accepted by ACM CCS 2024!
- 2024.03.09: 🎉🎉 Accepted paper for presentation at the 45th IEEE Symposium on Security and Privacy!
📝 Publications
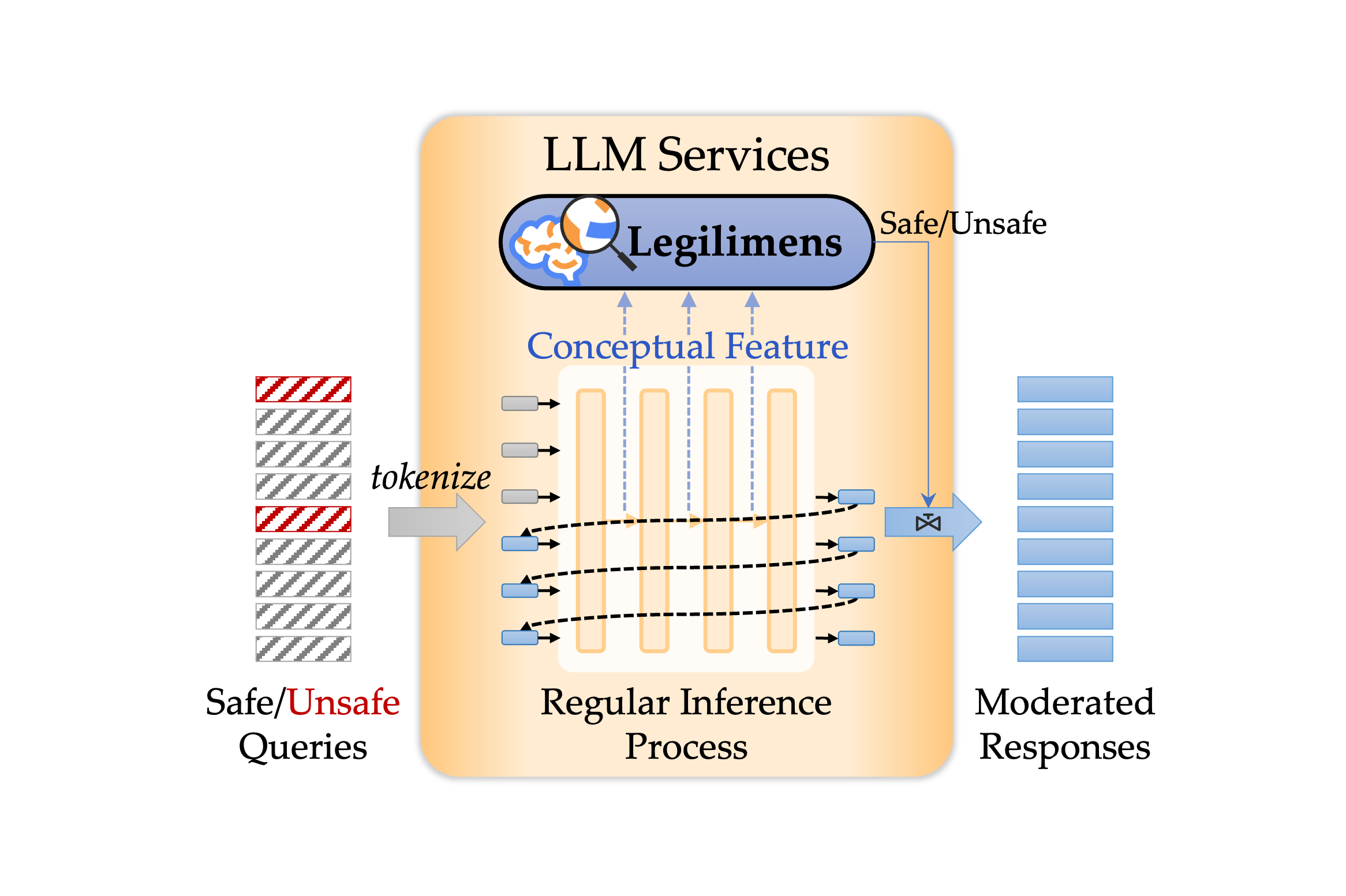
Legilimens: Practical and Unified Content Moderation for Large Language Model Services
Jialin Wu, Jiangyi Deng (co-first), Shengyuan Pang, Yanjiao Chen, Jiayang Xu, Xinfeng Li, Wenyuan Xu
- In this paper, we reveal for the first time that effective and efficient content moderation can be achieved by extracting conceptual features from chat-oriented LLMs, despite their initial fine-tuning for conversation rather than content moderation. We propose a practical and unified content moderation framework for LLM services, named Legilimens, which features both effectiveness and efficiency.
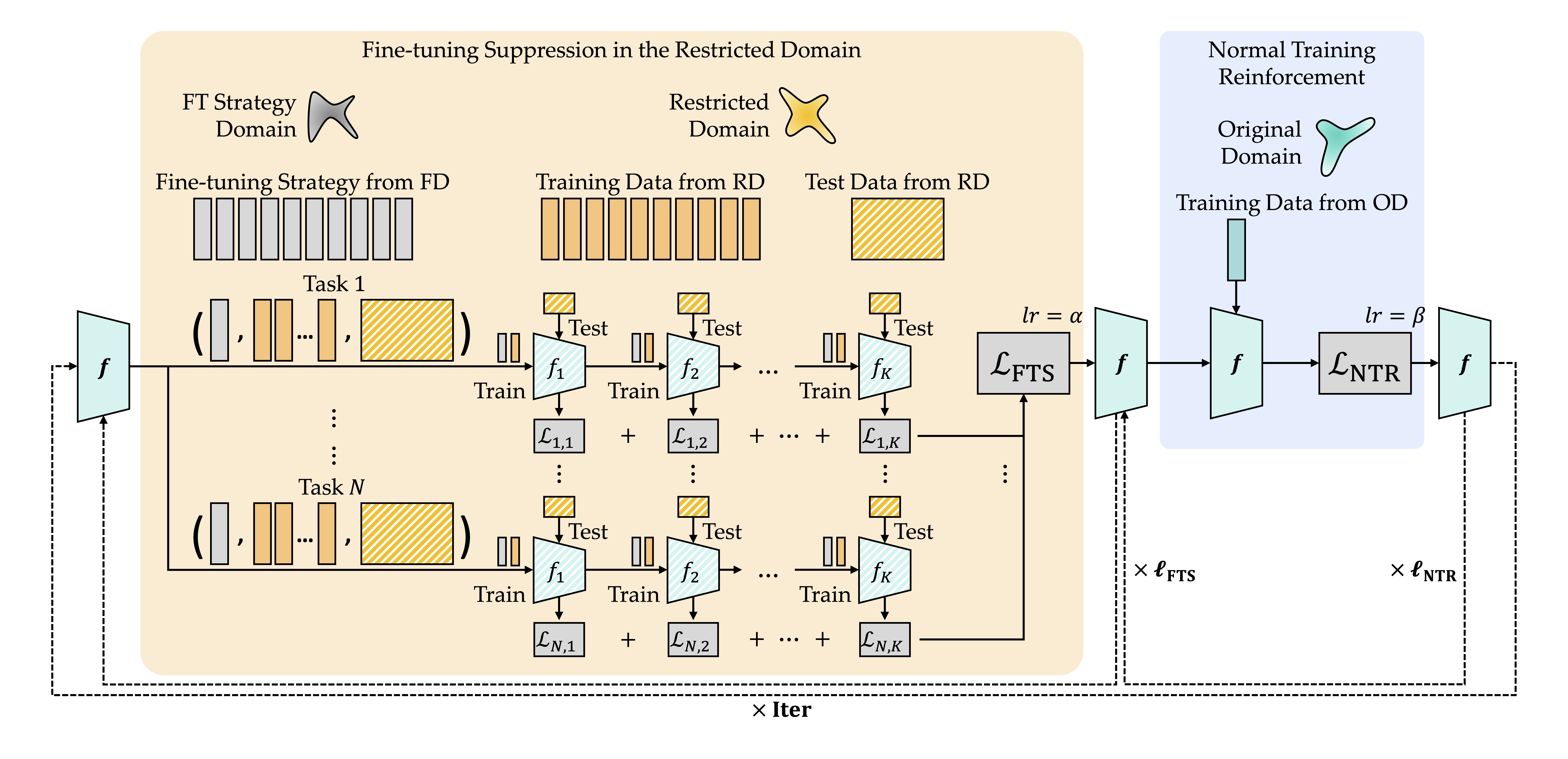
SOPHON: Non-Fine-Tunable Learning to Restrain Task Transferability For Pre-trained Models
Jiangyi Deng, Shengyuan Pang, Yanjiao Chen, Liangming Xia, Yijie Bai, Haiqin Weng, Wenyuan Xu
- In this paper, we introduce a pioneering learning paradigm, non-fine-tunable learning, which prevents the pre-trained model from being fine-tuned to indecent tasks while preserving its performance on the original task.
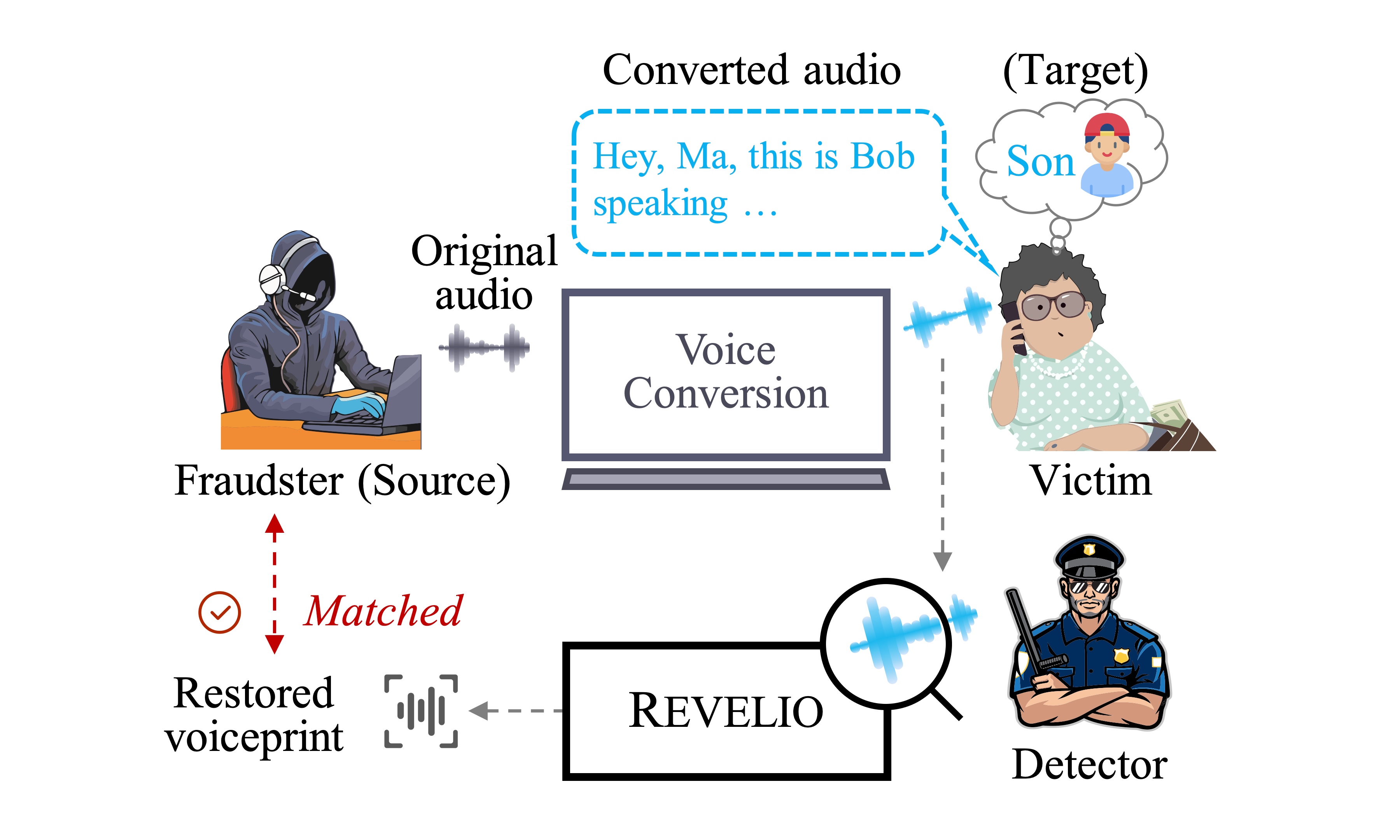
Catch You and I Can: Revealing Source Voiceprint Against Voice Conversion
Jiangyi Deng, Yanjiao Chen, Yinan Zhong, Qianhao Miao, Xueluan Gong, Wenyuan Xu
- In this paper, we make the first attempt to restore the source voiceprint from audios synthesized by voice conversion methods with high credit. This technique may assist investigations of voice conversion-based phone scam.
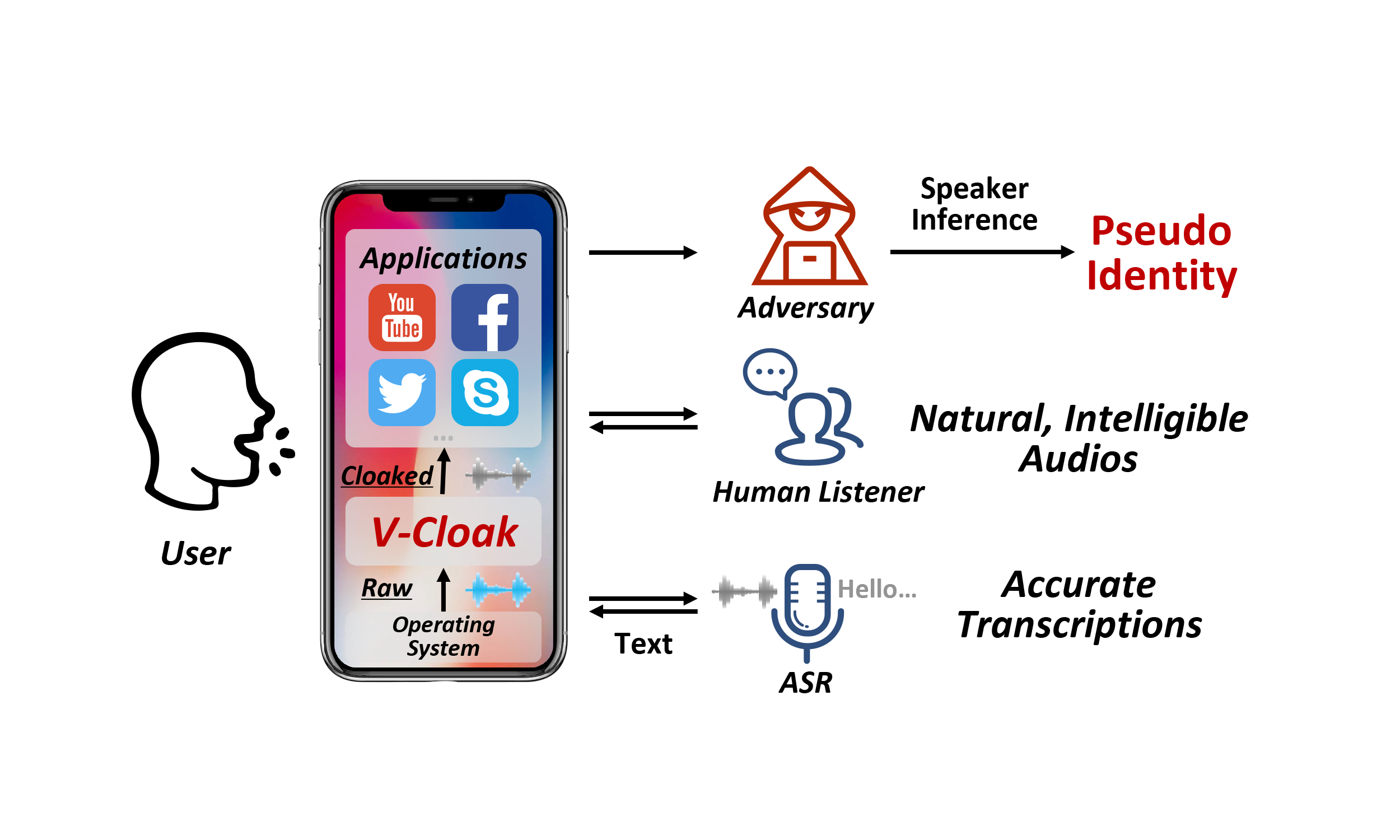
V-Cloak: Intelligibility-, Naturalness- & Timbre-Preserving Real-Time Voice Anonymization
Jiangyi Deng, Fei Teng, Yanjiao Chen, Xiaofu Chen, Zhaohui Wang, Wenyuan Xu
- In this paper, we develop a voice anonymization system, named V-Cloak, which attains real-time voice anonymization while preserving the intelligibility, naturalness and timbre of the audio.
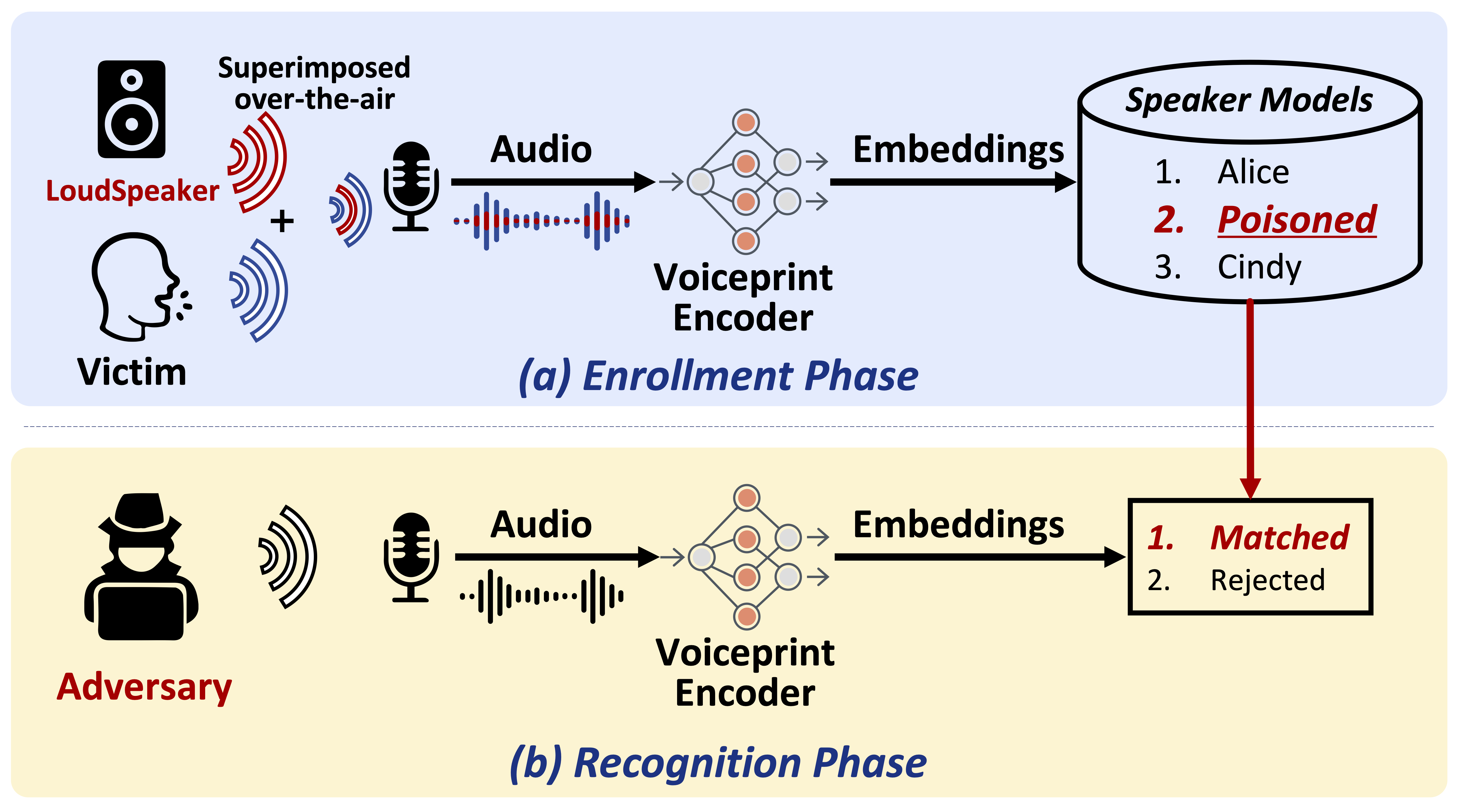
Jiangyi Deng, Yanjiao Chen, Wenyuan Xu
- In this paper, we explore a new attack surface of SRSs by presenting an enrollment-phase attack paradigm, named FenceSitter, where the adversary poisons the SRS using imperceptible adversarial ambient sound when the legitimate user registers into the SRS.
-
SafeGen: Mitigating Unsafe Content Generation in Text-to-Image Models. Xinfeng Li, Yuchen Yang, Jiangyi Deng (co-first), Chen Yan, Yanjiao Chen, Xiaoyu Ji, Wenyuan Xu. ACM CCS, 2024.
-
Alchemy: Data-Free Adversarial Training. Yijie Bai, Zhongming Ma, Yanjiao Chen, Jiangyi Deng, Shengyuan Pang, Yan Liu, Wenyuan Xu. ACM CCS, 2024.
-
Dr. Defender: Proactive Detection of Autopilot Drones based on CSI. Jiangyi Deng, Xiaoyu Ji, Beibei Wang, Bin Wang, Wenyuan Xu. IEEE TIFS, 2023.
-
A Nonlinearity-based Secure Face-to-Face Device Authentication for Mobile Devices. Xiaoyu Ji, Xinyan Zhou, Chen Yan, Jiangyi Deng, Wenyuan Xu. IEEE TMC, 2020.
-
Nauth: Secure face-to-face device authentication via nonlinearity. Xinyan Zhou, Xiaoyu Ji, Chen Yan, Jiangyi Deng, Wenyuan Xu. IEEE INFOCOM, 2019.
🎖 Honors and Awards
- 2024.09: ACM SIGSAC China Doctoral Dissertation award, ACM SIGSAC China
- 2024.03: Sun Youxian Scholarship, Zhejiang University
- 2024.03: Outstanding Graduate, Zhejiang University
- 2023.10: National Scholarship, Zhejiang University
- 2023.09: Outstanding Graduate Student Cadre, Zhejiang University
- 2023.09: Outstanding Graduate Student, Zhejiang University
- 2022.09: Outstanding Graduate Student Cadre, Zhejiang University
- 2020.09: Outstanding Graduate Student, Zhejiang University
📖 Services
- Reviewer of IEEE Transactions on Information Forensics and Security
- Reviewer of ACM Transactions on Privacy and Security
- External Reviewer of “Big Four”, i.e., IEEE S&P, USENIX Security, ACM CCS, and NDSS
- Teaching Assistant of AI and IOT, at Zhejiang University, 2021.9 - 2022.1, 2022.9 - 2023.1
- Teaching Assistant of Computer Networking, at Zhejiang University, 2020.9 - 2021.1, 2021.2 - 2021.6
💻 Internships
- 2023.05 - 2024.02, Department of Fundamental Security, Ant Group, China.
